Configure Networking for Protected Traffic Between the Site-To-Site Peers
After completing the configuring of the Site-To-Site connection, make sure that you perform the following configuration for VPN to function on all targeted devices.
Procedure
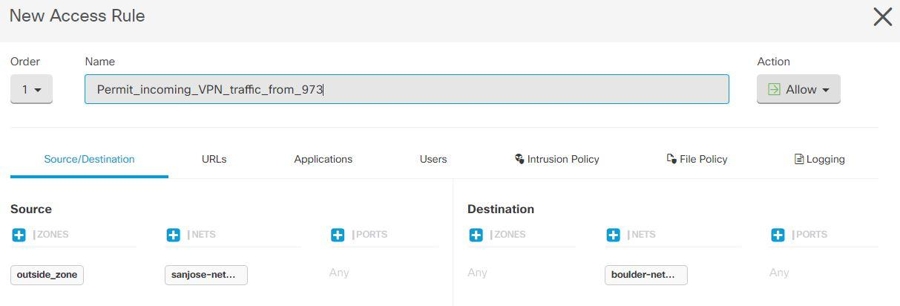
Step 1 | Configure AC policies: Configure AC policies for permitting bidirectional traffic between the protected networks behind both peers. These policies help the packets to traverse to the intended destination without being dropped.
After creating AC policies on one device, you must create similar policies on its peer. | ||
Step 2 | If NAT is configured on either of the peer devices, you need to configure the NAT exempt rules manually. See Exempting Site-to-Site VPN Traffic from NAT. | ||
Step 3 | Configure routing for receiving the return VPN traffic on each peer.
After configuring routing settings on one device, you must configure similar settings on its peer. |