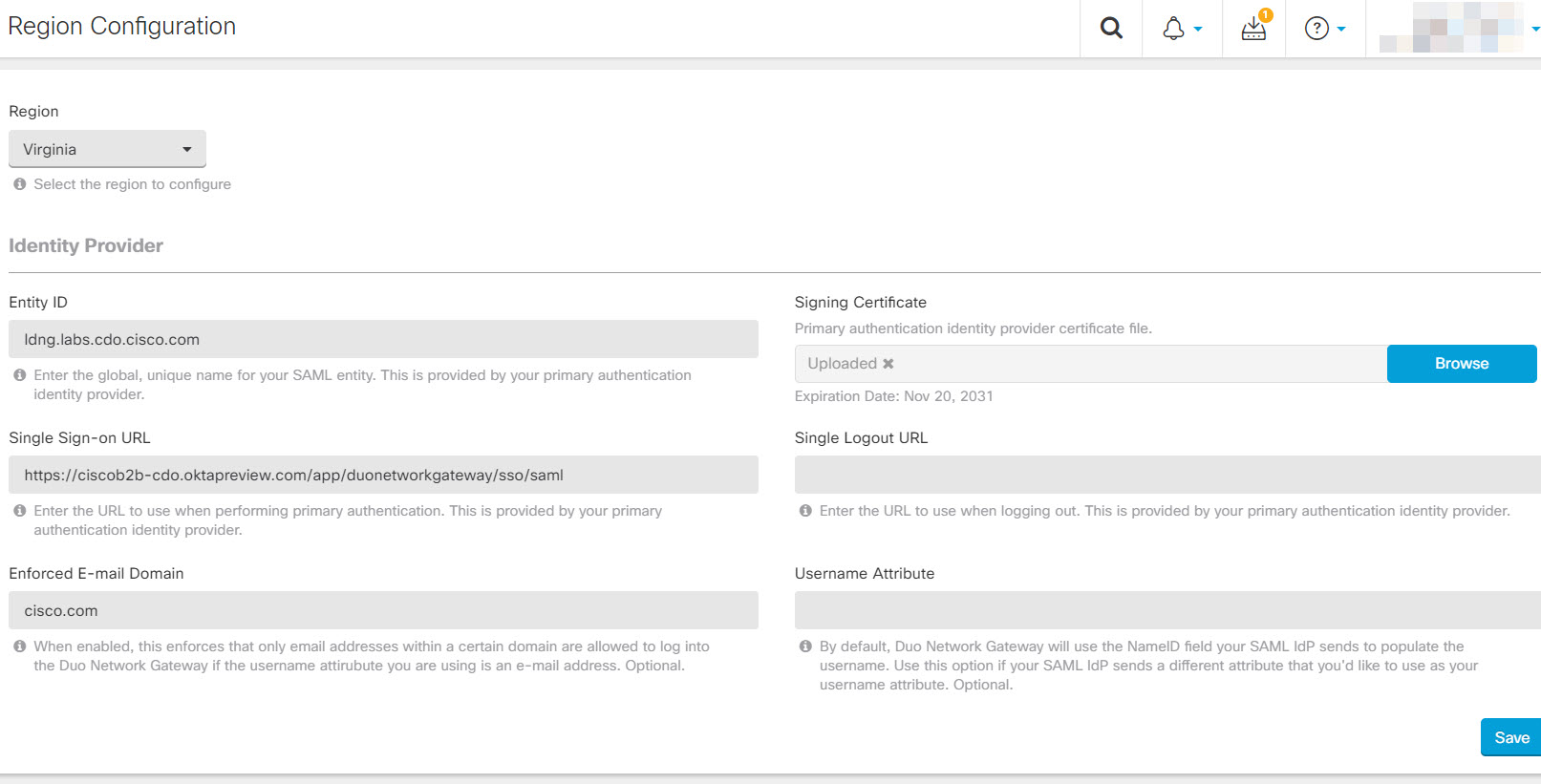
A region is equivalent to an Secure Firewall Cloud Native cluster onboarded into CDO. You must provide the information of the Identity Provider (IDP) the DNG must contact to authenticate a user attempting to access protected applications without a VPN connection.
SFCN DNG requires a SAML 2.0 Identity Provider (IdP) to use as its primary authentication source. You can integrate a third-party IdP such as Okta or Azure by completing the following steps:
Procedure
| Step 1 | In the navigation bar, choose Secure Firewall Cloud Native > Region Configuration. |
| Step 2 | In the Region list, select a Secure Firewall Cloud Native associated with the region you want to configure.
Note |
A message appears prompting you to create a support request if the selected Secure Firewall Cloud Native associated with a region has no configuration.
|
|
| Step 3 | In the DNS Resolution area, you can provide global internal DNS resolvers per region to resolve the Fully Qualified Domain Names (FQDN) of your internal URLs into IP addresses. Secure Firewall Cloud Native resolves the FQDNs using the DNS resolvers in the specified order. |
| Step 4 | Configure the following fields:
-
Entity ID: Copy the Entity ID or Issuer ID from the IdP page and paste it here. It is the global unique name from your identity provider for your SAML entity. Your primary authentication identity provider provides this information.
Example for Okta: http://www.okta.com/abc1a2bcd3efG4HIj5K6
Example for Azure: https://samltoolkit.azurewebsites.net
-
Signing Certificate: Primary authentication identity provider certificate file.
-
Single Sign-on URL: Copy the Assertion Consumer Service URL or Single Sign-On URL from the IdP page and paste it here to use when performing primary authentication. Your primary authentication identity provider provides this information.
Example for Okta: https://example.okta.com/app/duonetworkgateway/abc1a2bcd3efG4HIj5K6/sso/saml
Example for Azure: https://samltoolkit.azurewebsites.net/
-
Single Logout URL: Enter the URL to use when logging out. Your primary authentication identity provider provides this information.
-
Enforced E-mail Domain: This is an optional setting. Enabling this will allow you to enforce that only e-mail addresses within a certain domain are allowed to log into Duo Network Gateway if the username attribute you are using is an e-mail address.
-
Username Attribute: This is an optional setting. By default, Duo Network Gateway will use the NameID field your SAML IdP sends to populate the username. Use this option if your SAML IdP sends a different attribute that you'd like to use as your username attribute.
|
| Step 5 | Click Save. |