How It Works
This topic discusses the architecture of the Dynamic Attributes Connector.
The following figure shows how the system functions at a high level.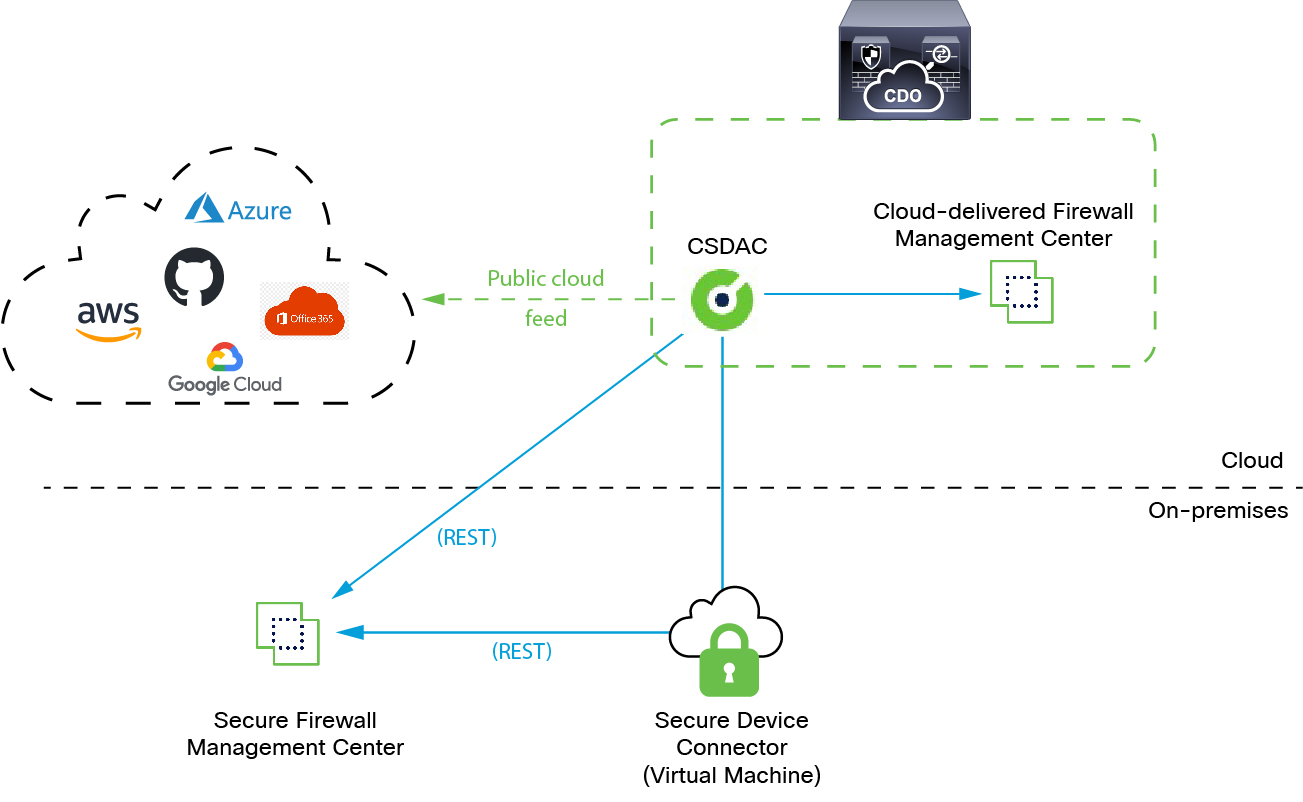
-
The system supports certain public cloud providers.
This topic discusses supported connectors (which are the connections to those providers).
-
The dynamic attributes connector is provided with Security Cloud Control; it includes a Cloud-Delivered Firewall Management Center adapter and you can connect to an On-Prem Firewall Management Center using the Secure Device Connector.
For more information about the Secure Device Connector, see Secure Device Connector (SDC).
-
The adapter defined by the dynamic attributes connector receives those dynamic attributes filters as dynamic objects and enables you to use them in access control rules.
You can create the following types of adapters:
-
On-Prem Firewall Management Center for an on-premises device.
This type of device might be managed by Security Cloud Control or it might be a standalone.
-
Cloud-Delivered Firewall Management Center for devices managed by Security Cloud Control.
-