System Flow for Duo RADIUS Secondary Authentication
Following is an explanation of the system flow: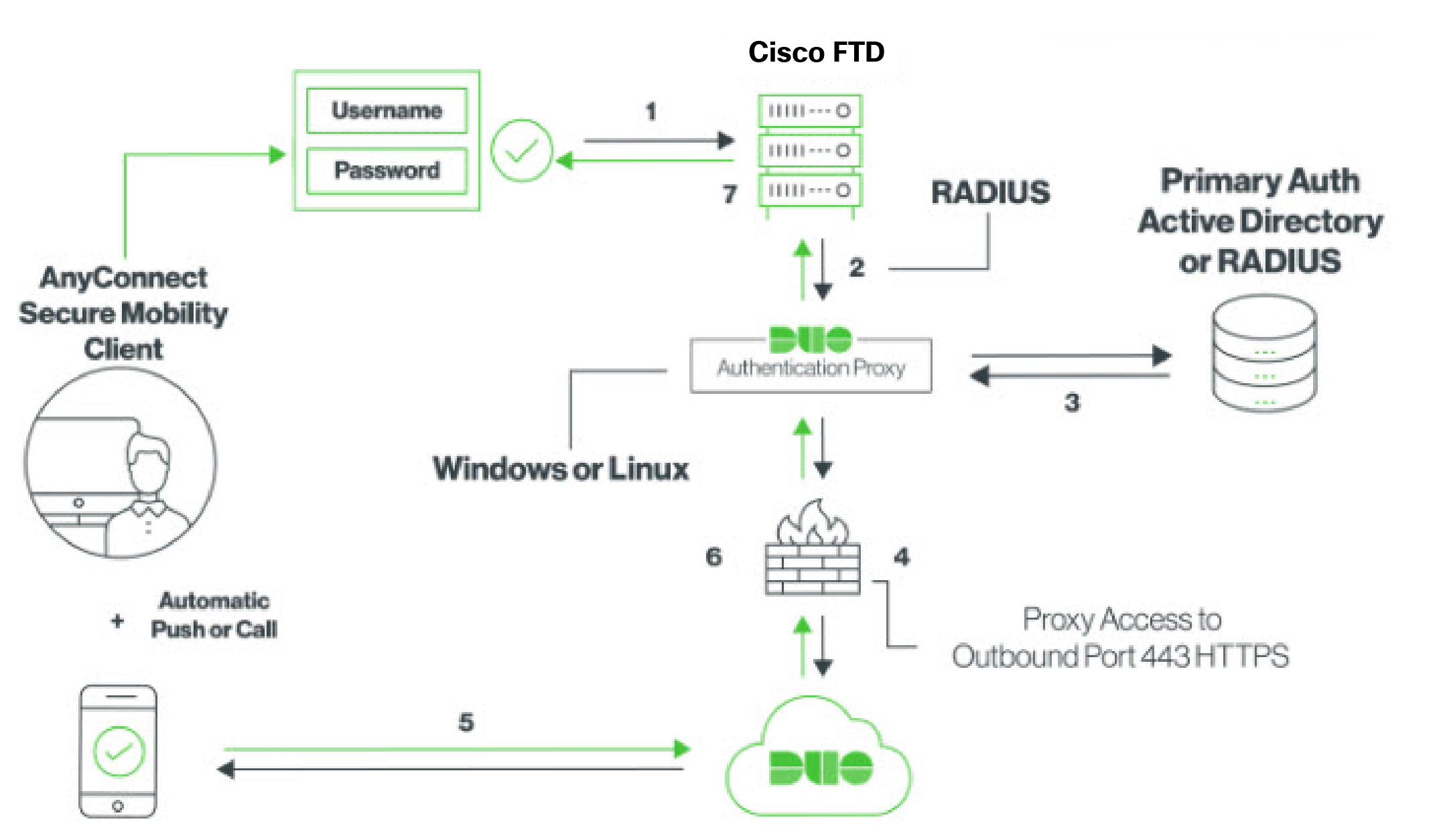
-
The user makes a remote access VPN connection to the FDM-managed device and provides username associated with RADIUS/AD server, the password for the username configured in the RADIUS/AD server, followed by one of the DUO codes, Duo-password, push, SMS, or phone. For more information, Duo Two-Factor Authentication Using RADIUS
-
FDM-managed device sends the authentication request to the Duo Authentication proxy.
-
Duo Authentication proxy authenticates this primary authentication attempt with the primary authentication server, which might be Active Directory or RADIUS.
-
If the credentials are authenticated, the Duo Authentication Proxy connection is established to Duo Security over TCP port 443.
-
Duo then authenticates the user separately through push notification, text message with a passcode, or a telephone call. The user must complete this authentication successfully.
-
Duo authentication proxy receives the authentication response.
-
If the secondary authentication was successful, the FDM-managed device establishes a remote access VPN connection with the user’s AnyConnect client.