Export the Active Directory server's root certificate
The task that follows discusses how to export the Active Directory server's root certificate, which is required to connect securely to the Firewall Management Center to obtain user identity information.
These tasks apply to Microsoft Active Directory only. If you use LDAP, consult an appropriate reference for the procedure.
Before you begin
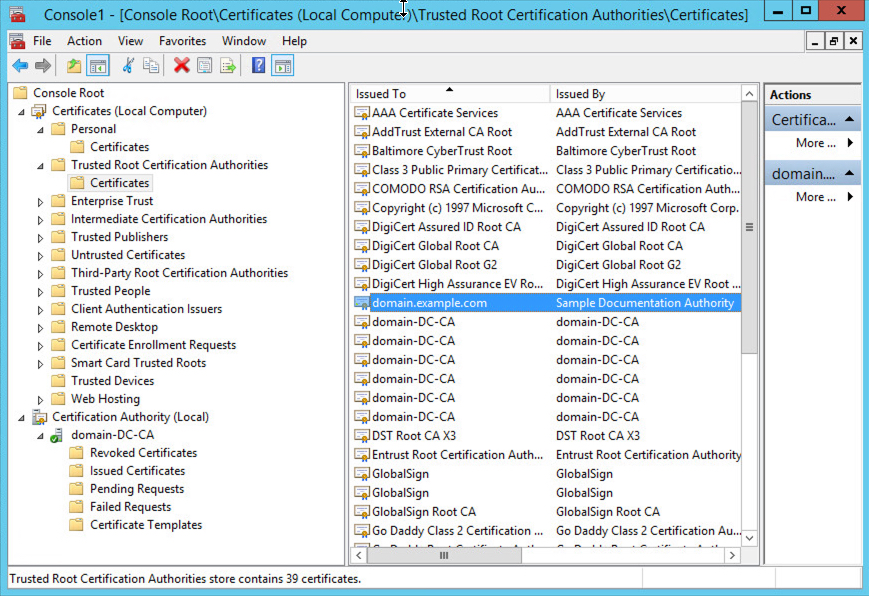
You must know the name of your Active Directory server's root certificate. The root certificate might have the same name as the domain or the certificate might have a different name. The procedure that follows shows one way you can find the name; there could be other ways, however.
Procedure
Step 1 | Following is one way to find the name of the Active Directory Server's root certificate; consult Microsoft documentation for more information: |
Step 2 | Export the certificate using the certutil command. This is only one way to export the certificate. It's a convenient way to export the certificate, especially if you can run a web browser and connect to the Firewall Management Center from the Active Directory server. |