Change the Manager Access Interface from Management to Data
You can manage the Firewall Threat Defense from either the dedicated Management interface or from a data interface. If you want to change the manager access interface after you added the device to the Firewall Management Center, follow these steps to migrate from the Management interface to a data interface. To migrate the other direction, see Change the Manager Access Interface from Data to Management.
Initiating the manager access migration from Management to data causes the Firewall Management Center to apply a block on deployment to the Firewall Threat Defense. To remove the block, enable manager access on the data interface.
See the following steps to enable manager access on a data interface and also configure other required settings.
Procedure
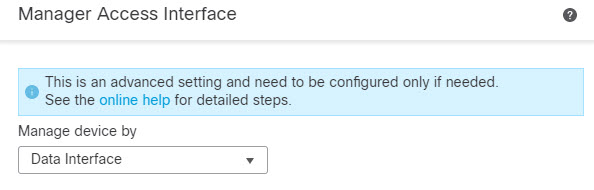
Step 1 | Initiate the interface migration. |
Step 2 | Enable manager access on the data interface. Click Interfaces, click Edit ( Check Enable management access and click OK. By default, all networks are allowed, but you can limit access as long as the Firewall Management Center address is allowed. If the manager access interface uses a static IP address, you are reminded to configure routing for it. Click Save on the Interfaces page. You can enable manager access on one routed data interface. Make sure this interface is fully configured with a name and IP address and that it is enabled. |
Step 3 | (Optional) If you use DHCP for the interface, enable the web type DDNS method on the DDNS page. Navigate to , and then click DDNS under the DHCP tab. DDNS ensures the Firewall Management Center can reach the Firewall Threat Defense at its Fully-Qualified Domain Name (FQDN) if the FTD's IP address changes. |
Step 4 | Make sure the Firewall Threat Defense can route to the Firewall Management Center through the data interface; add a static route if necessary on the Static Route page. Navigate to and then click Static Route under the Routing tab. |
Step 5 | (Optional) Configure DNS in a Platform Settings policy: choose , and click DNS. Apply the policy to this device. DNS is required if you use DDNS. You may also use DNS for FQDNs in your security policies. |
Step 6 | (Optional) Enable SSH for the data interface in a Platform Settings policy, and apply it to this device at page. Click Edit ( SSH is not enabled by default on the data interfaces, so if you want to manage the Firewall Threat Defense using SSH, you need to explicitly allow it. |
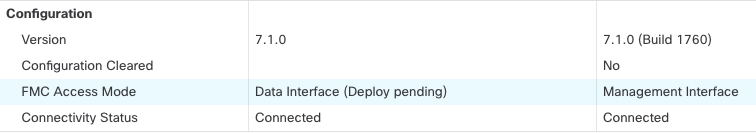
Step 7 | You will see a validation error to confirm that you are changing the manager access interface. Check Ignore warnings and deploy again. The Firewall Management Center will deploy the configuration changes over the current Management interface. After the deployment, the data interface is now ready for use, but the original management connection to Management is still active. |
Step 8 | At the Firewall Threat Defense CLI (preferably from the console port), set the Management interface to use a static IP address and set the gateway to use the data interfaces. configure network {ipv4 | ipv6} manual ip_address netmask data-interfaces
We recommend that you use the console port instead of an SSH connection because when you change the Management interface network settings, your SSH session will be disconnected. |
Step 9 | If necessary, re-cable the Firewall Threat Defense so it can reach the Firewall Management Center on the data interface. |
Step 10 | In the Firewall Management Center, disable the management connection, update the Host IP address for the Firewall Threat Defense in the page in the Management area under the Device tab, and reenable the connection. See Update the Hostname or IP Address in the Firewall Management Center. If you used the Firewall Threat Defense hostname or just the NAT ID when you added the Firewall Threat Defense to the Firewall Management Center, you do not need to update the value; however, you need to disable and reenable the management connection to restart the connection. |
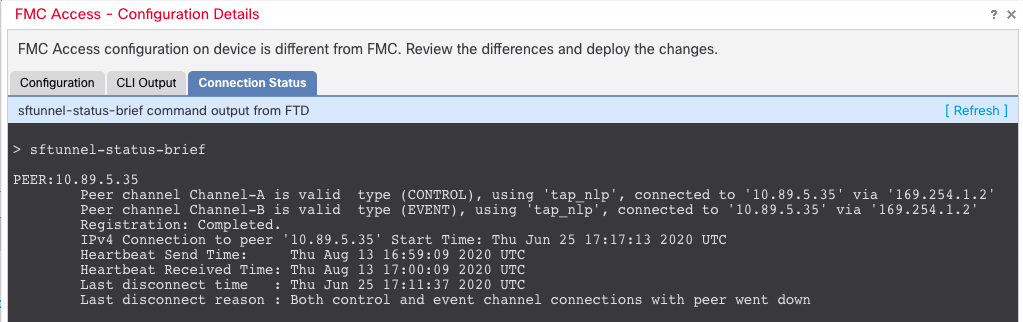
Step 11 | Ensure the management connection is reestablished. In the page, click FMC Access: Configuration and then click Connection Status. Alternatively, you can check at the Firewall Threat Defense CLI. Enter the sftunnel-status-brief command to view the management connection status. The following status shows a successful connection for a data interface, showing the internal "tap_nlp" interface.
If it takes more than 10 minutes to reestablish the connection, you should troubleshoot the connection. See Troubleshoot Management Connectivity on a Data Interface. |