Configure the Captive Portal Part 1: Create an Identity Policy
Before you begin
This five-part procedure shows how to set up the captive portal using the default TCP port 885 and using a CDO server certificate for both the captive portal and for SSL decryption. Each part of this example explains one task required to enable the captive portal to perform active authentication.
If you follow all the steps in this procedure, you can configure captive portal to work for users in your domains. You can optionally perform additional tasks, which are discussed in each part of the procedure.
For an overview of the entire procedure, see How to Configure the Captive Portal for User Control.
Procedure
| Step 1 | Log in to the CDO if you have not already done so. | ||
| Step 2 | Click and create or edit an identity policy. | ||
| Step 3 | (Optional.) Click Add Category to add a category for the captive portal identity rules and enter a Name for the category. | ||
| Step 4 | Click Active Authentication. | ||
| Step 5 | Choose the appropriate Server Certificate from the list
or click Add (
| ||
| Step 6 | From the Redirect to Host Name field, click the network object you previously created. | ||
| Step 7 | Enter 885 in the Port field and specify the Maximum login attempts. | ||
| Step 8 | (Optional.) Choose an Active Authentication Response Page as described in Captive Portal Fields. The following figure shows an example. 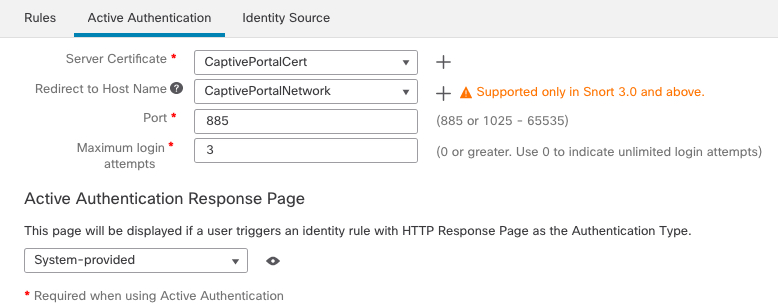 | ||
| Step 9 | Click Save. | ||
| Step 10 | Click Rules. | ||
| Step 11 | Click Add Rule to add a new captive portal identity policy rule, or click Edit ( | ||
| Step 12 | Enter a Name for the rule. | ||
| Step 13 | From the Action list, choose Active Authentication. The system can enforce captive portal active authentication on HTTP and HTTPS traffic only. If an identity rule Action is Active Authentication (you are using captive portal) or if you are using passive authentication and you check the option on Realms & Settings page to Use active authentication if passive or VPN identity cannot be established, use TCP ports constraints only. | ||
| Step 14 | Click Realm & Settings. | ||
| Step 15 | From the Realms list, choose a realm to use for user authentication. A realm sequence is not supported. | ||
| Step 16 | (Optional.) Check Identify as Guest if authentication cannot identify user. For more information, see Captive Portal Fields. | ||
| Step 17 | Choose an Authentication Protocol from the list. | ||
| Step 18 | (Optional.) To exempt specific application traffic from captive portal, see Exclude Applications from Captive Portal. | ||
| Step 19 | Add conditions to the rule (port, network, and so on) as discussed in Identity Rule Conditions. | ||
| Step 20 | Click Add. | ||
| Step 21 | At the top of the page, click Save. |
What to do next
Continue with Configure the Captive Portal Part 2: Create a TCP Port Access Control Rule.
 )
) )
)