Step 1 | Configure FTD Radius Server Object.
-
In the left pane, click Manage > Objects.
-
Click  > RA VPN Objects (ASA & FTD) > Identity Source. > RA VPN Objects (ASA & FTD) > Identity Source.
-
Provide a name and set the Device Type as FTD.
-
Select Radius Server Group and click Continue.
-
In the Radius Server section, click the Add button and click Create New Radius Server.
In the Server Name or IP Address field, enter your Duo Authentication Proxy server's fully-qualified hostname or IP address. 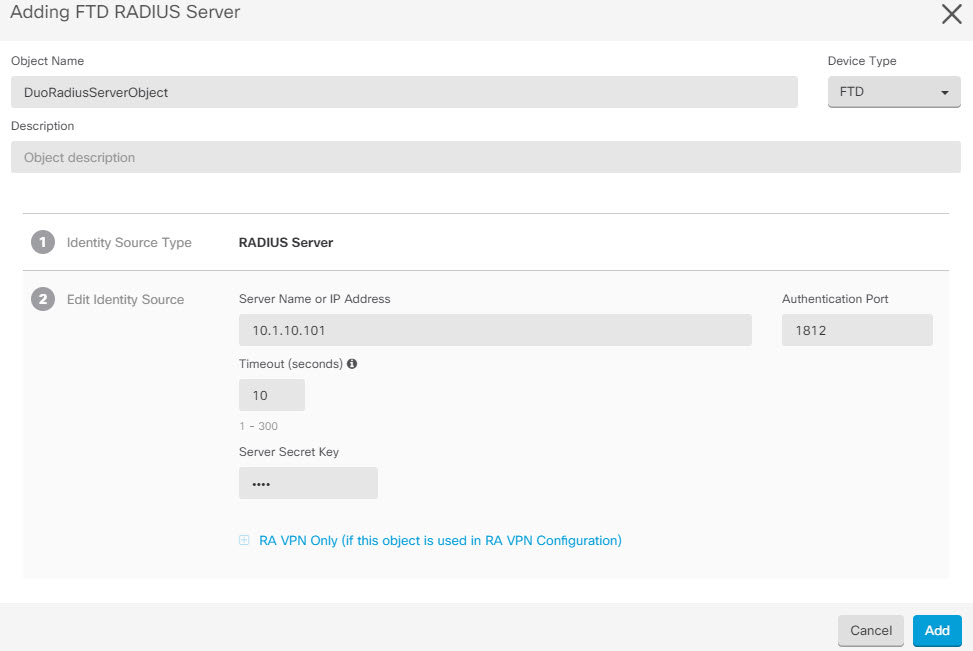
-
Once you have added the Duo RADIUS server to the group, click Add to create the new Duo RADIUS server group.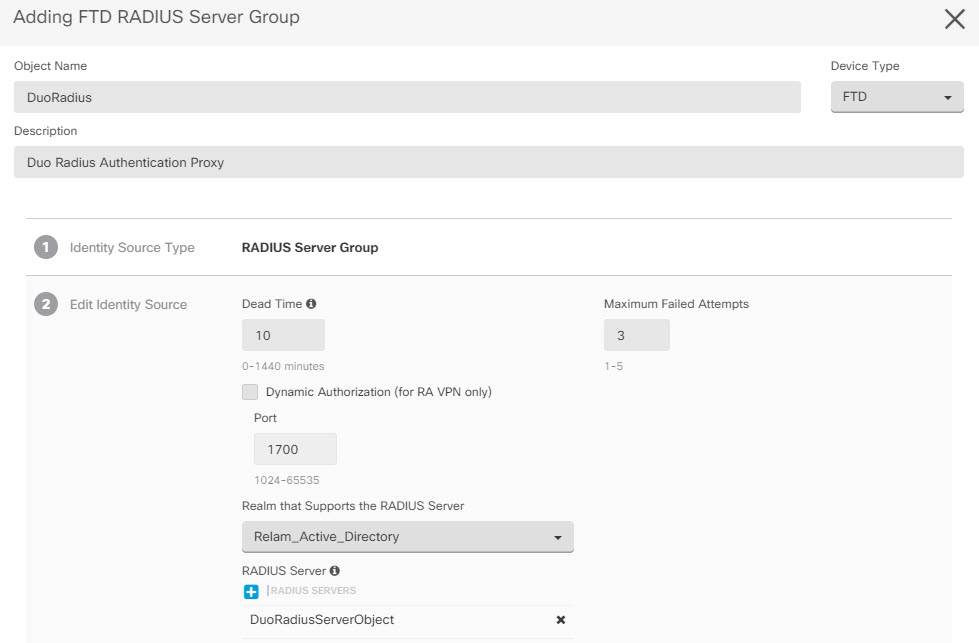
|
Step 2 | Change the Remote Access VPN Authentication Method to Duo RADIUS.
-
In the left pane, click .
-
Expand the VPN configuration and click on the connection profile to which you want to add Duo.
-
In the Actions pane on the right, click Edit.
-
Select the Authentication Type can be AAA or AAA and Client Certificate.
-
In the Primary Identity Source for User Authentication list, select the server group you created earlier.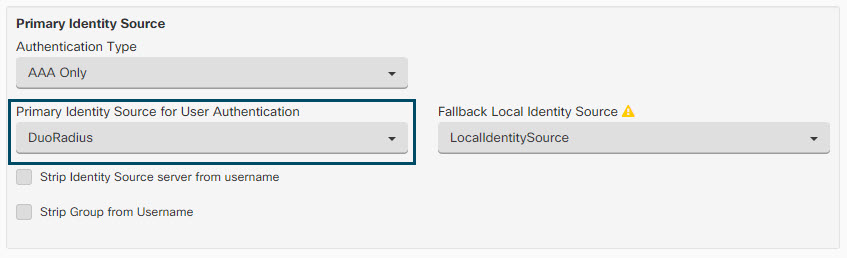
-
You typically do not need to select an "Authorization Server" or "Accounting Server".
-
Click Continue.
-
In the Summary and Instructions step, click Done to save the configuration.
|
Step 3 | Review and deploy now the changes you made, or wait and deploy multiple changes at once. |
 >
> 

