Realms and trusted domains
When you configure a Microsoft Active Directory (AD) realm in the Firewall Management Center, it is associated with a Microsoft Active Directory or LDAP domain.
A grouping of Microsoft Active Directory (AD) domains that trust each other is commonly referred to as a forest. This trust relationship can enable domains to access each other's resources in different ways. For example, a user account defined in domain A can be marked as a member of a group defined in domain B.
The system and trusted domains
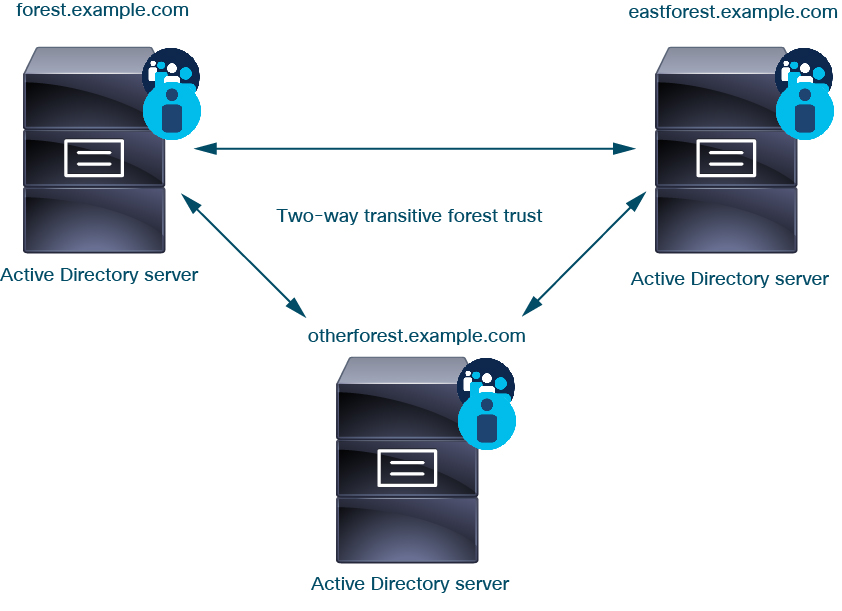
The system supports AD forests that are configured in a trust relationship. There are several types of trust relationships; this guide discusses two-way, transitive forest trust relationships. The following simple example shows two forests: forest.example.com and eastforest.example.com . Users and groups in each forest can be authenticated by AD in the other forest, provided you configure the forests that way.
If you set up the system with one realm for each domain and one directory for each domain controller, the system can discover up to 100,000 foreign security principals (users and groups). If these foreign security principals match a user downloaded in another realm, then they can be used in access control policy.
You need not configure a realm for any domain that has no users you wish to use in access control policies.

To continue the example, suppose you have three AD forests (one of which could be a subdomain or an independent forest), all set up as two-way transitive forest relationships, all users and groups are available in all three forests as well as in the system. (As in the preceding example, all three AD domains must be set up as realms and all domain controllers must be configured as directories in those realms.)
Finally, you can set up the Firewall Management Center to be able to enforce identity policies on users and groups in a two-forest system with two-way transitive forest trust. Suppose each forest has at least one domain controller, each of which authenticates different users and groups. For the Firewall Management Center to be able to enforce identity policies on those users and groups, you must set up each domain containing relevant users as Firewall Management Center realm and each domain controller as Firewall Management Center directory in the respective realm.
Failure to properly configure the Firewall Management Center prevents some of the users and groups from being able to be used in policies. You will see warnings when you try to synchronize users and groups in that case.

Using the preceding example, set up the Firewall Management Center as follows:
-
Realm for any domain in forest.example.com that contains users you want to control with access control policies
-
Directory in the realm for AMERICAS.forest.example.com
-
Directory in the realm for ASIA.forest.example.com
-
-
Realm for any domain in eastforest.example.com that contains users you want to control with access control policies
-
Directory in the realm for EUROPE.eastforest.example.com
-
Note | The Firewall Management Center uses the AD field msDS-PrincipalName to resolve references to find user and group names in each domain controller. msDS-PrincipalName returns a NetBIOS name. |