TLS server identity discovery
The latest version of the Transport Layer Security (TLS) protocol 1.3, defined by RFC 8446, is the preferred protocol for many web servers to provide secure communications. Because the TLS 1.3 protocol encrypts the server's certificate for additional security, and the certificate is needed to match application and URL filtering criteria in access control rules, the Firepower System provides a way to extract the server certificate without decrypting the entire packet.
You can enable this feature, referred to as TLS server identity discovery, when you configure advanced settings for an access control policy. Certain features are not supported, such as STARTTLS traffic, the HTTP CONNECT method, and in a network where another device is already decrypting traffic.
When a new connection starts that will be affected by TLS server identity discovery, the Firewall Threat Defense holds the original ClientHello packet to determine the identity of the server to which it connects before continuing. The Firewall Threat Defense device sends a specialized connection from the Firewall Threat Defense to the server. The server's response includes the server certificate, the specialized connection is terminated, and the original connection is evaluated as required by the access control policy.
TLS server identity discovery prioritizes the certificate's Common Name (CN) over the Server Name Indication (SNI).
To enable TLS server identity discovery, click the Advanced tab, click Edit ( ) for the setting, and select Early application detection and URL categorization.
) for the setting, and select Early application detection and URL categorization.
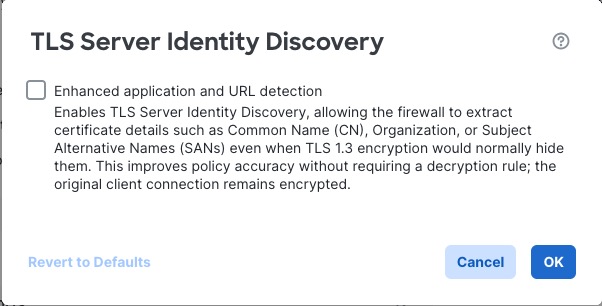
We strongly recommend enabling it for any traffic you want to match on application or URL criteria, especially if you want to perform deep inspection of that traffic. An SSL policy is not required because traffic is not decrypted in the process of extracting the server certificate.
Note |
|